Protecting web applications from attack is a key priority for nearly any business transacting or connecting with customers online. A key reason why is the broad range of adverse impacts organizations can face when application attacks are successful (see Figure 1).1
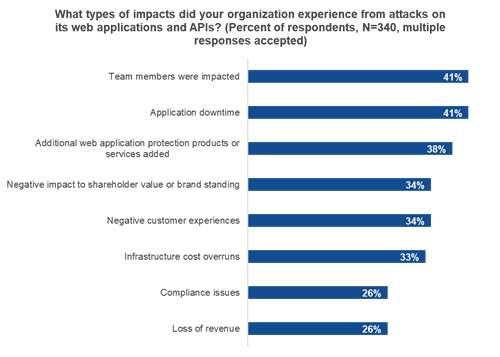
Some of the most notable include:
Poor customer experience. At a minimum, an attack can affect application availability. While this can be a minor inconvenience for customers, if sensitive customer data is stolen the ramifications can be much more significant.
Compliance issues. The Payment Card Industry Data Security Standard (PCI DSS), Digital Operations Resilience Act, and General Data Protection Regulation are key regulations which apply to many types of businesses. Failure to comply can lead to fines, bad publicity, and even customer lawsuits.
Financial repercussions. Whether due to a direct loss of revenue due to downtime, impact to shareholder value, or the additional costs incurred following an attack, impacts to the bottom line can be significant.
1. Source: Enterprise Strategy Group Research Report, Trends in Modern Application Protection, July 2022.