DSPM deployments involve a combination of technology, people, and processes to discover and categorize data stores to identify weaknesses, prioritize risks, and ensure data remains protected from evolving threats on an ongoing basis. The scale of operations varies across enterprises as one might expect, but on average the initial phase of locating, categorizing, and establishing policies takes four to six months for most enterprises (see Figure 1). DSPM projects involve a variety of constituents and can touch complex environments residing both in the cloud and on premises.

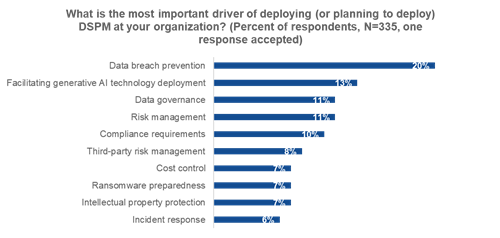
Enterprises deploy DSPM to address a number of issues. As shown in Figure 2, the most prevalent use case is preventing a potential data breach (20%), followed by facilitating the deployment of GenAI technology (13%). Enterprises want to know where their sensitive data is stored and categorize what is inside of their data stores so they can take steps to avoid potential data leakage and loss. In the case of GenAI, locating and categorizing data used to inform large language models can help avoid potentially sensitive information making its way into a model and subsequently being inadvertently leaked.