Figure 1. Current Threat Landscape Sentiment

Figure 2. Security Incidents Organizations Have Experienced Over the Past 24 Months

Figure 3. Consequences of the Security Incidents Organizations Have Experienced Over the Past 24 Months

Figure 4. Primary Drivers of Organization’s Cybersecurity Strategy

Figure 5. Cyber Supply Chain Security Sentiment

Figure 6. Why Organizations Believe Cyber Supply Chain Security Is Becoming More Difficult

Figure 7. Most Important Security Considerations During Product Evaluation and Purchasing Processes
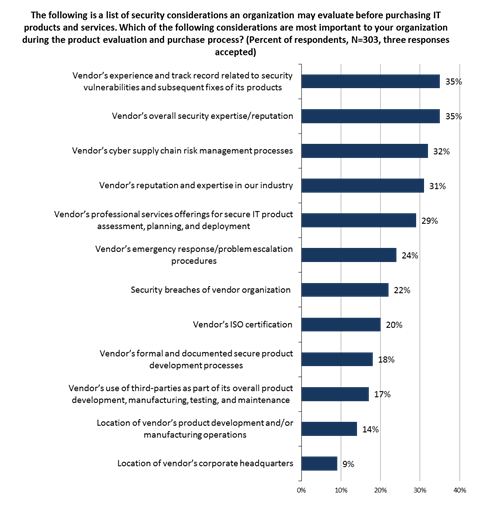
Figure 8. Audits of Strategic Suppliers

Figure 9. Internal Groups Responsible for IT Vendor Security Audit Processes

Figure 10. Mechanisms Used to Conduct IT Vendor Security Audits

Figure 11. Current IT Vendor Security Audit Process

Figure 12. Measurement of IT Vendor Security Audits

Figure 13. Respondents Rate IT Vendors’ Commitment to/Communications about Internal Security Processes and Procedures

Figure 14. Confidence Level in Organization’s Knowledge of the Purchasing Origin of Hardware and Software

Figure 15. Use of Suspect Vendors

Figure 16. Internal Software Development

Figure 17. Confidence Level in Security of Internally Developed Software

Figure 18. Security Incidents Related to the Compromise of Internally Developed Software

Figure 19. Security Activities Included as Part of the Software Development Process

Figure 20. Secure Software Development Initiatives
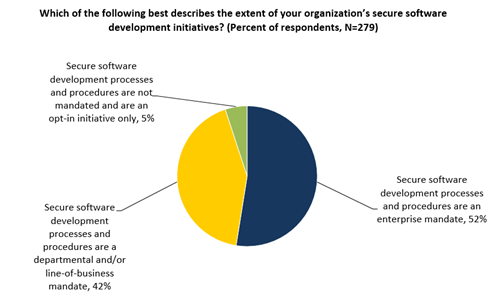
Figure 21. Why Organizations Chose to Establish a Secure Software Development Program

Figure 22. Plans to Include Security Activities as Part of the Software Development Process

Figure 23. Outsourcing of Software Maintenance or Development Activities

Figure 24. Security Safeguards Mandated of Service Providers

Figure 25. Sharing of IT Services or Business Applications with Third Parties

Figure 26. Approximate Number of External Third Parties with which Respondent Organizations Share IT Services or Business Applications

Figure 27. Security Controls Partners Require When Receiving IT Services or Business Applications from Critical Infrastructure Organizations

Figure 28. Security Controls Critical Infrastructure Organizations Require When Using IT Services or Business Applications from Third Parties

Figure 29. Groups Responsible for Security Policies and Safeguards for Interaction with Third Parties

Figure 30. Establishment of Security Policies and Safeguards for Interaction with Third Parties

Figure 31. Respondents’ Opinion of the U.S. Federal Government’s Cybersecurity Strategy

Figure 32. Role of the U.S. Federal Government with Regard to Cybersecurity
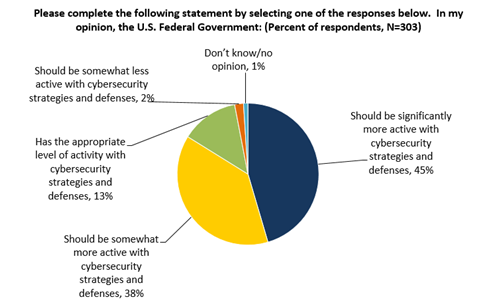
Figure 33. Suggested Actions for the U.S. Federal Government with Regard to Cybersecurity

Figure 34. Survey Respondents by Current Job Function

Figure 35. Survey Respondents by Number of Employees

Figure 36. Survey Respondents by Industry
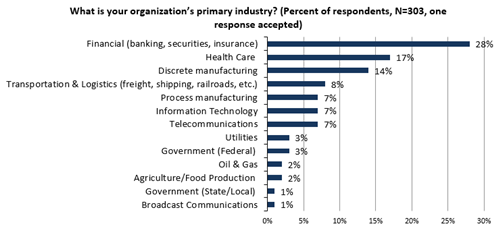
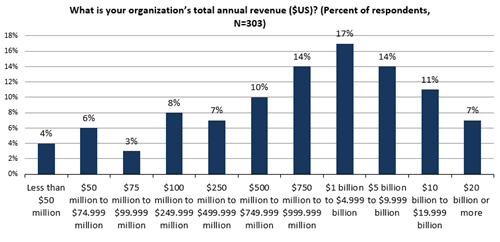
Figure 37. Survey Respondents by Annual Revenue